Typical Protection Scenario
With the Moway SDK, API and tools provided, Developer has capable to
implement comprehensive customize protection & licensing scheme to protect your
application.
With Moway USB Dongle, Tools and API, Developer may take either way to design and
implement a secure protection & license scheme quickly:
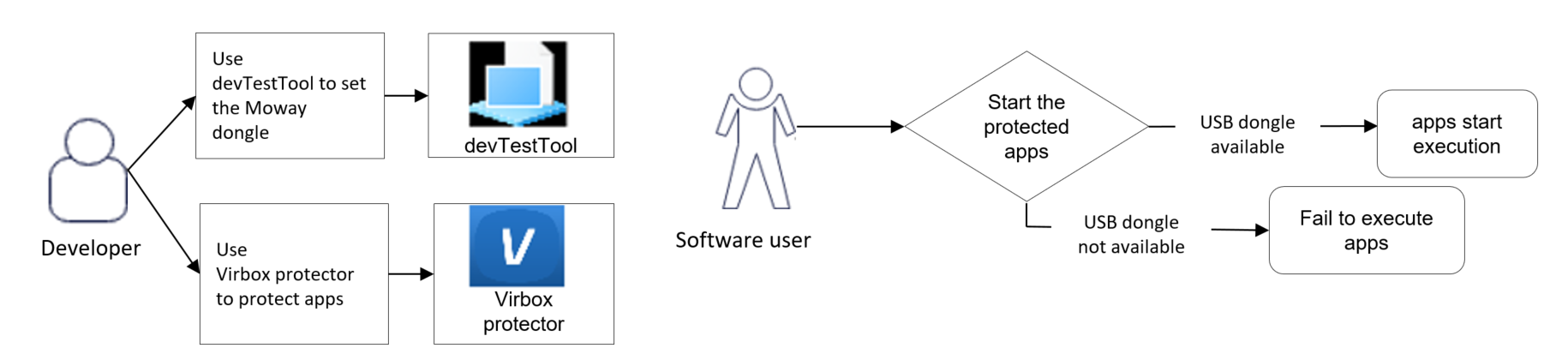
1. Use Moway tool chain, to complete and implement total protection and
licensing process with codeless. securely, quickly;
Build up and implement a securely & instant protection &
licensing scheme, especially
to those developer without rich experience & resource in copyright protection &
licensing.
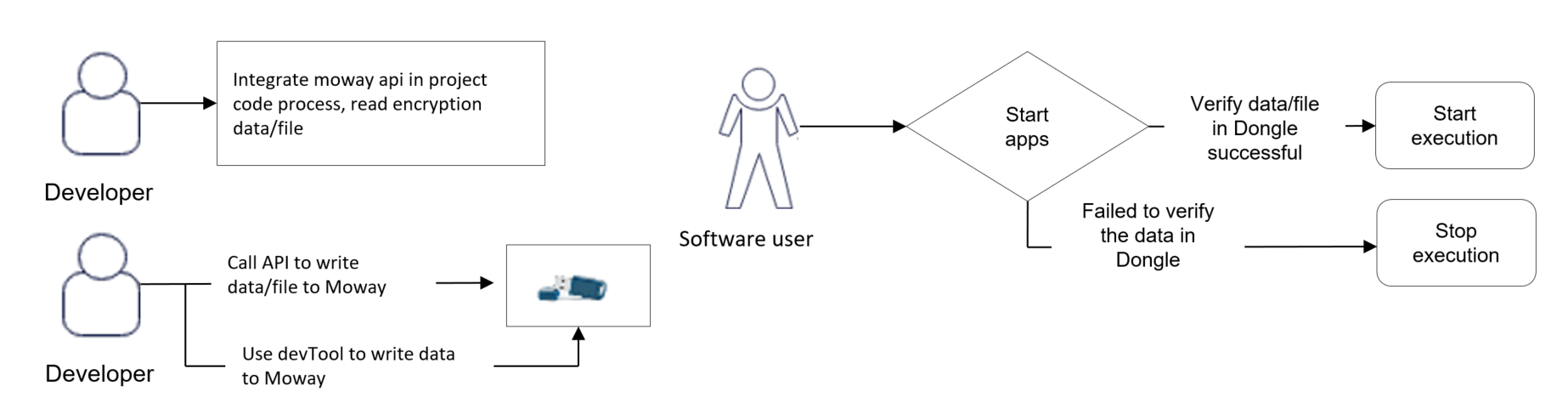
2. Integrate Moway API & library with your
project, Leverage multiple API to get the the most secure protection scheme:
Design, build up and implement a securely & customized
protection & licensing scheme, especially to those developer with rich experience &
resource in copyright protection & licensing.
2.1 Binding with hardware fingerprinting (binding with specific
Moway device, binding
with specific hardware machine),
2.2 Sign/signature verification (use
cryptographic algorithm),
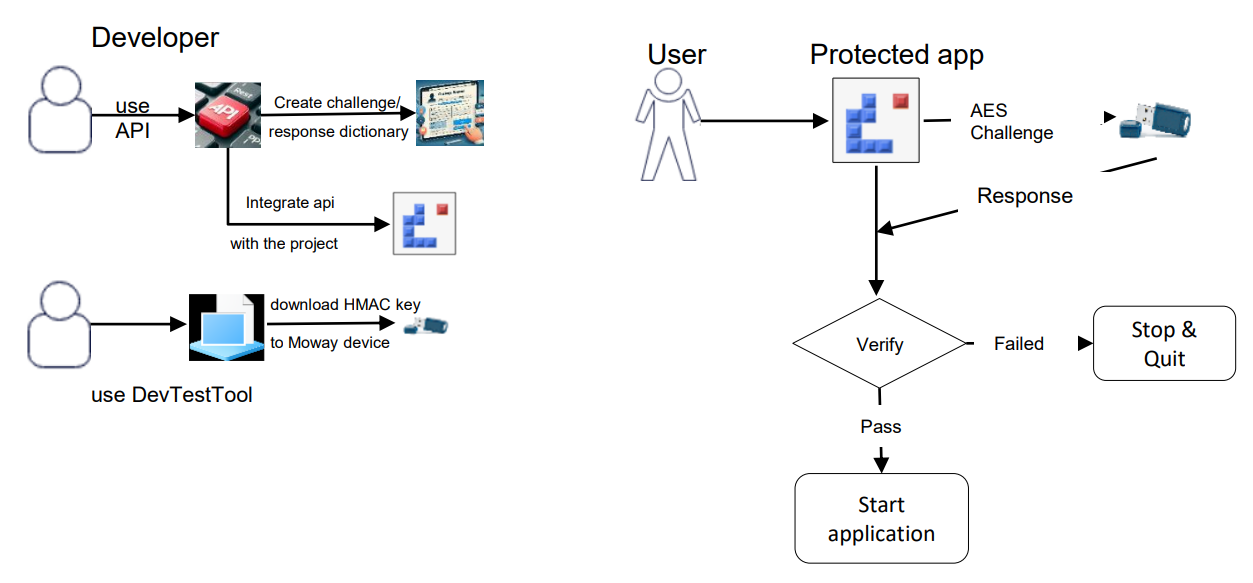
2.3 Challenge/response authentication,
2.4 Flexible
license terms: Licensing to each software functionality, License upgrade
etc.
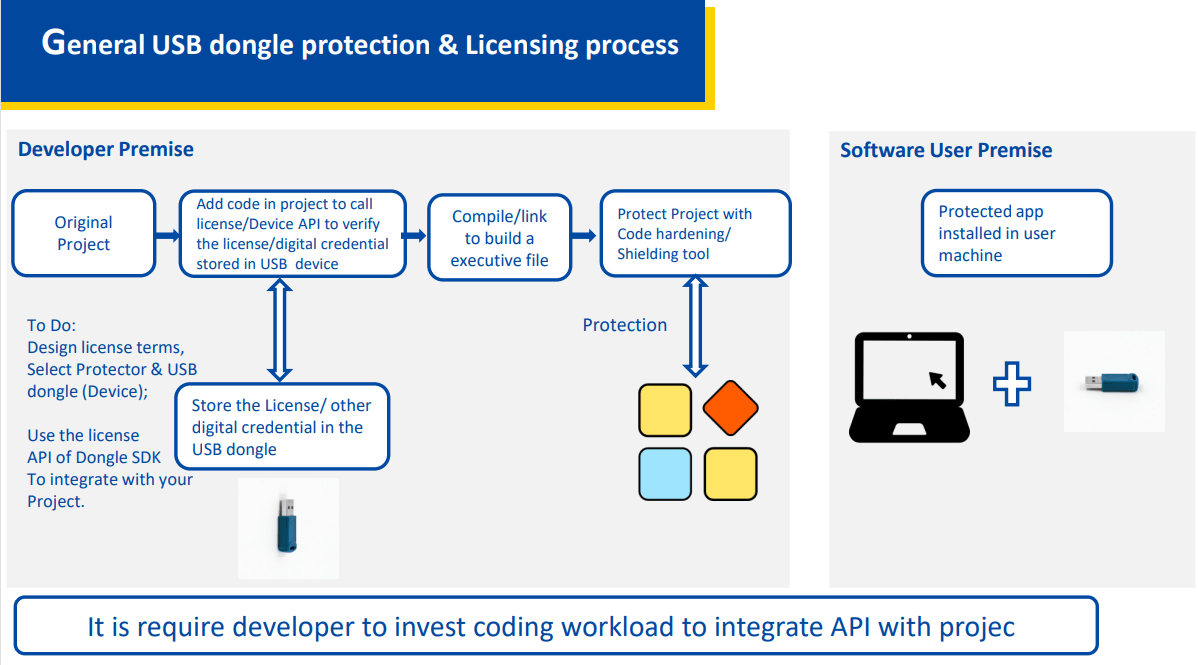
Solution Overview
Brief and introduce how to use Moway USB dongle to create & implement protection and
licensing scheme, it is quite useful overview to developer, especially for those
developer without enough experience in software protection and license. Download
Solution Overview
Use USB device to implement a customize protection & Licensing scheme.
Essential knowledge before to design tailor made protection &
License solution based on USB dongle
Moway: Typical Application Scenario
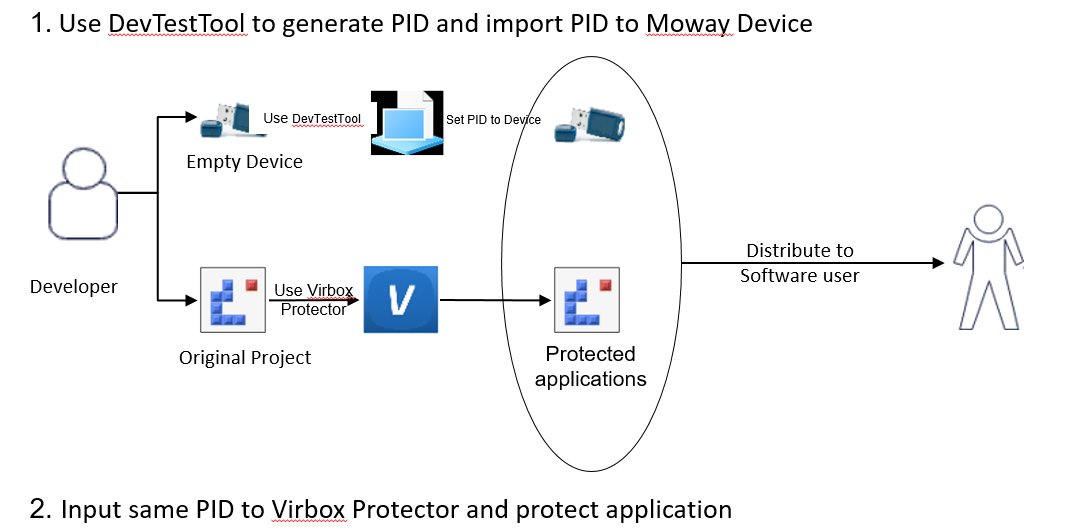
1. Use Moway PID to build up instant & secure protection scheme to
protect application
Applicable for those developer didn’t establish a license
management system; without enough resource, time investment, or protection
experience in software protection and not familiar how to use the USB dongle to
design & create a tailor made licensing scheme. and intent to build up simple and
secure “license” system to protect applications quickly and safety; with minimum
investment.
Implement the Moway instant protection
scheme;
Secure your applications, Save investment, Protect software
sales, Keep revenue
growth.
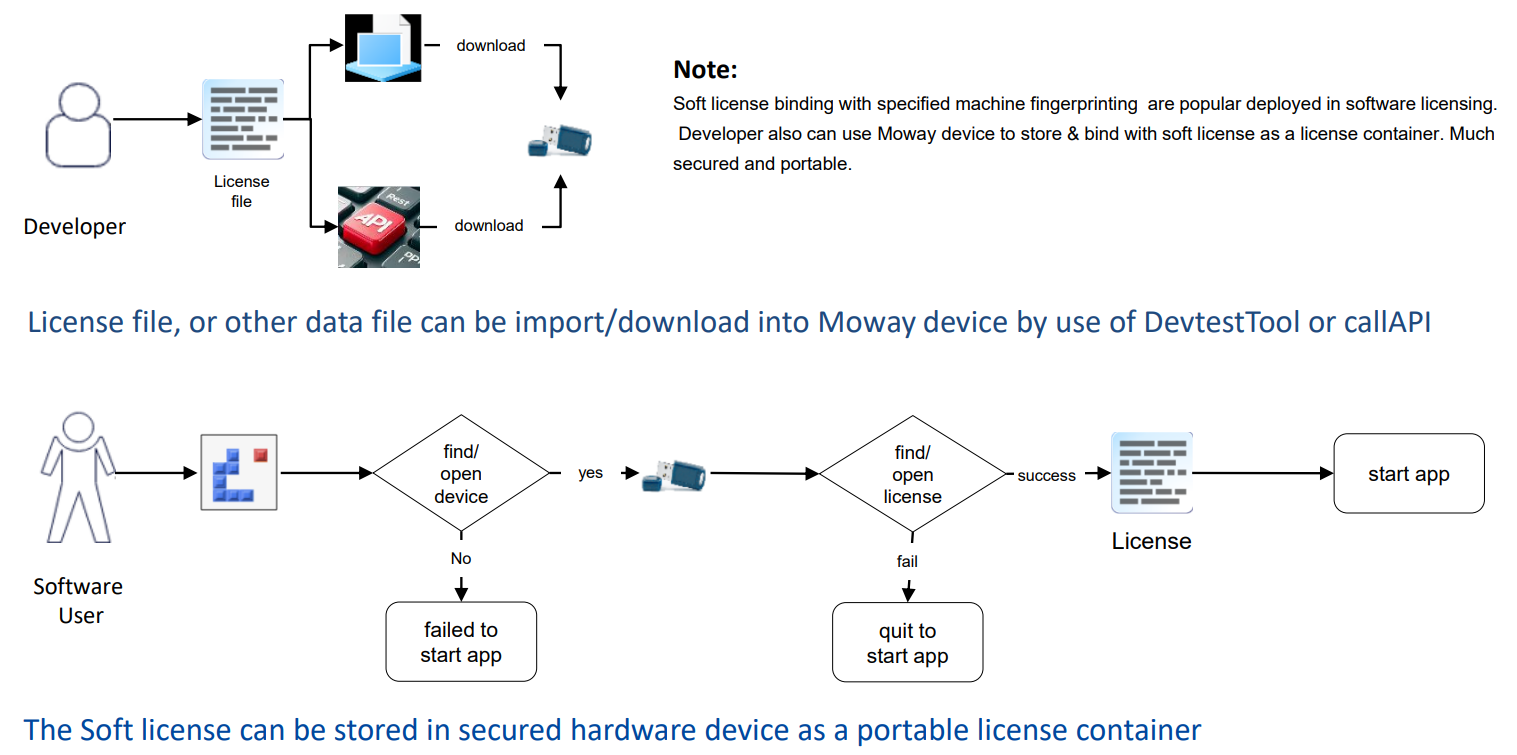
2. Use Moway to be the as secure & portable license container
For some developer has established & deployed License system (Self-established or
purchase third party license system, such as Flexera, Reprise, etc. besides soft
license binding with specific machine, they may consider to use USB hardware dongle
(Device) as a secure and portable license container to store the license file to
prevent the license being copied, cracked. Then Moway, as to be the more secure
container. will be the best option to those developer.
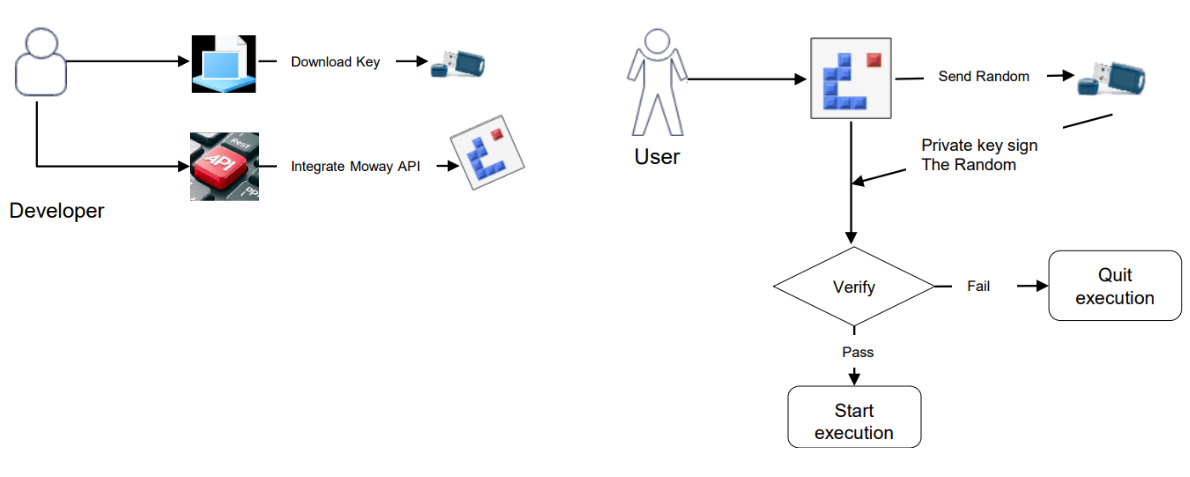
3. Identification of Genuine software by Sign/Signature verification
process with cryptographic key
Signing and signature verification process implemented to enhance security when developer
design a protection licensing scheme, to prevent application tampering or verify data
integrity. Here is sample to shown how to use signing and signature verification process
to identify the genuine software.
Asymmetry cryptographic algorithm (RSA) and key used in signing/signature verification
process.
The signing and signature verification process can be used in the similar protection
scheme and applicable for similar scenario.
4. Challenge/Response Authentication (Symmetric Cryptographic
Algorithm/API)